Secure Your Systems with Confidence
TaraQuant empowers teams with structured threat modeling, attack path analysis, and actionable risk insights for applications, embedded systems, and critical infrastructures.
Gain a holistic view of your security posture, identify vulnerabilities proactively, and streamline compliance with an intuitive, data-driven platform.
See TaraQuant in Action
Explore the intuitive interface designed for comprehensive security assessment. Click on any image to view details.
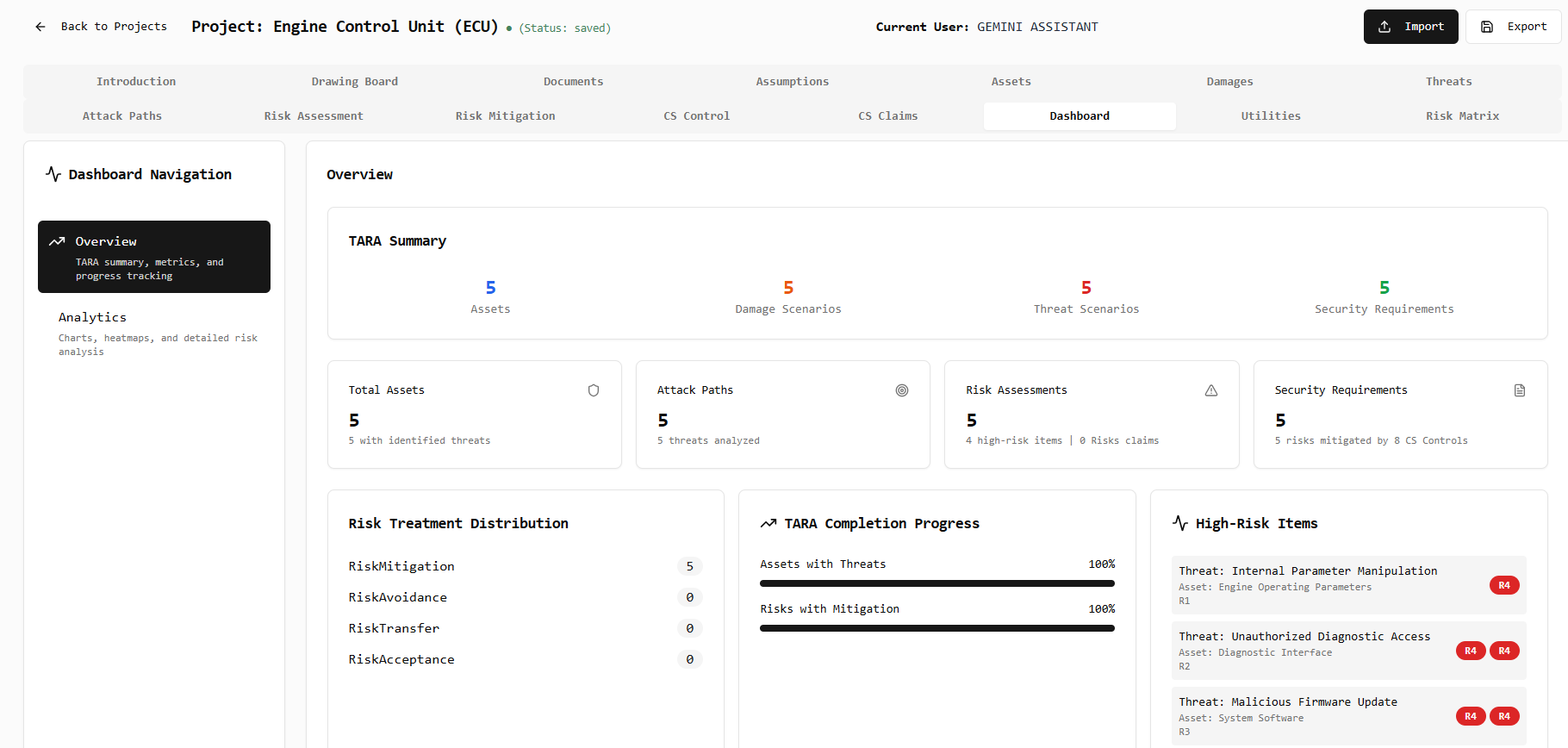
Dashboard Overview

The main dashboard provides a comprehensive overview of your security assessment progress, including key metrics, risk distribution, completion status, and high-risk items requiring immediate attention.
Comprehensive Security Assessment
Advanced threat modeling and risk assessment capabilities designed for security professionals, developers, and system architects.
Threat Modeling Framework
Build robust threat models by clearly defining assets, identifying potential damages, and linking them to specific threat scenarios. Our structured approach ensures comprehensive coverage of all critical system components.
Assets Management
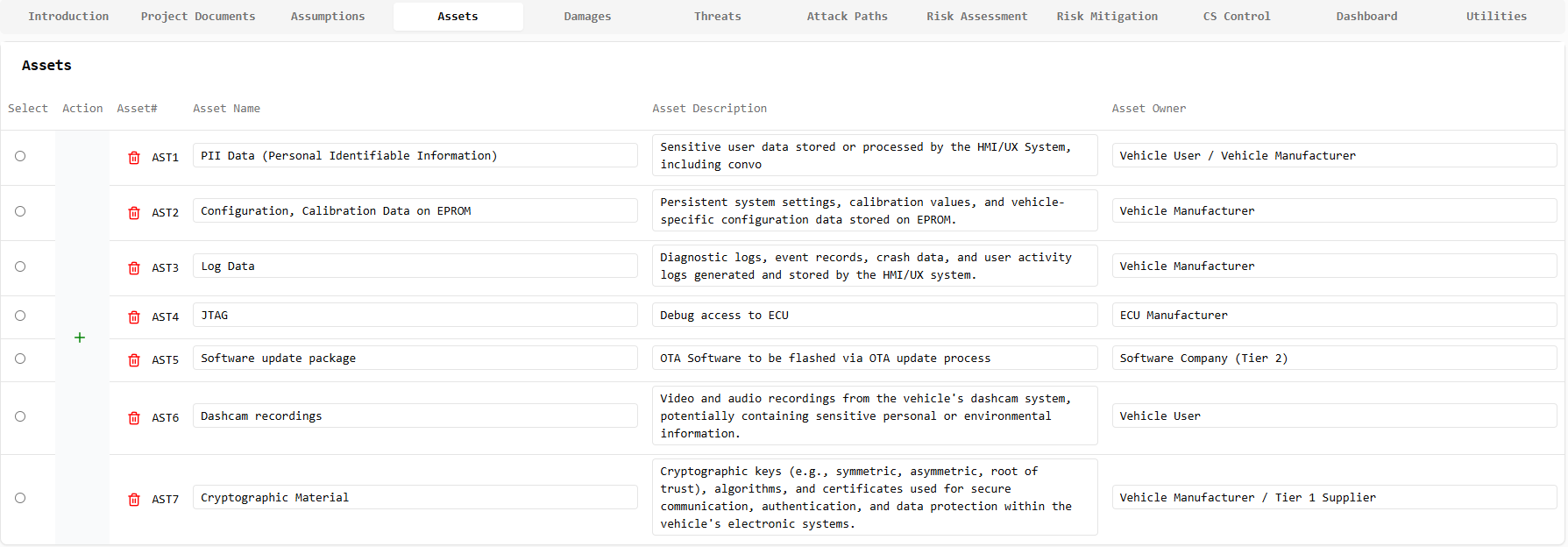
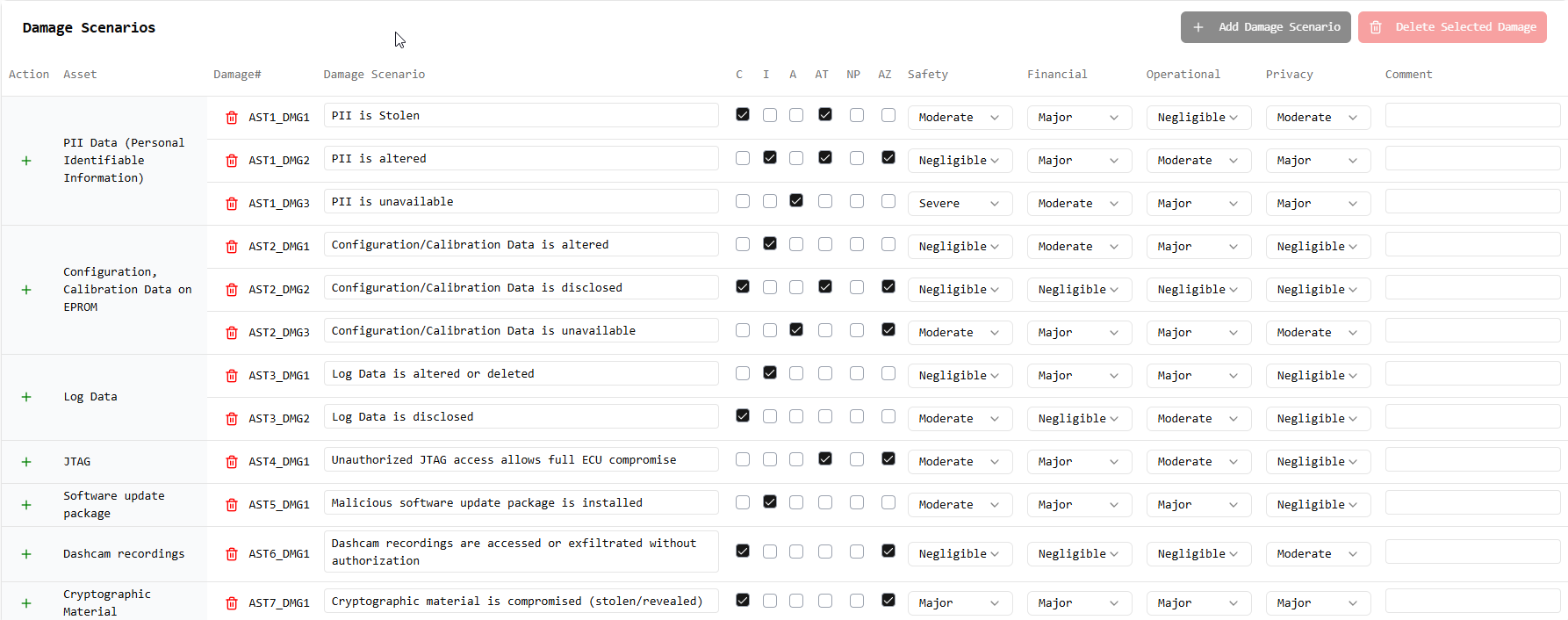
Damage Scenarios
Threat Scenarios

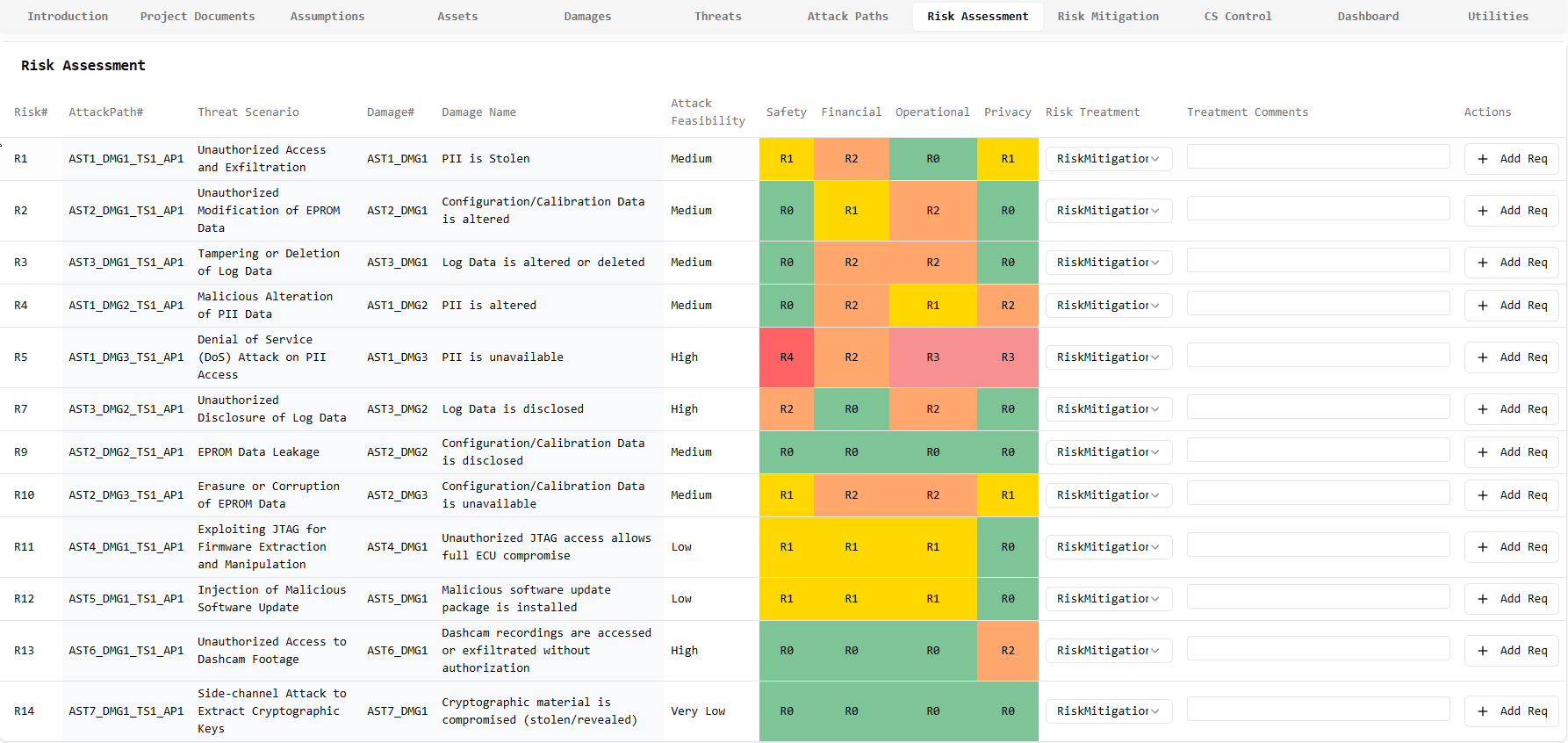
Risk Assessment Matrix
Analytics Dashboard
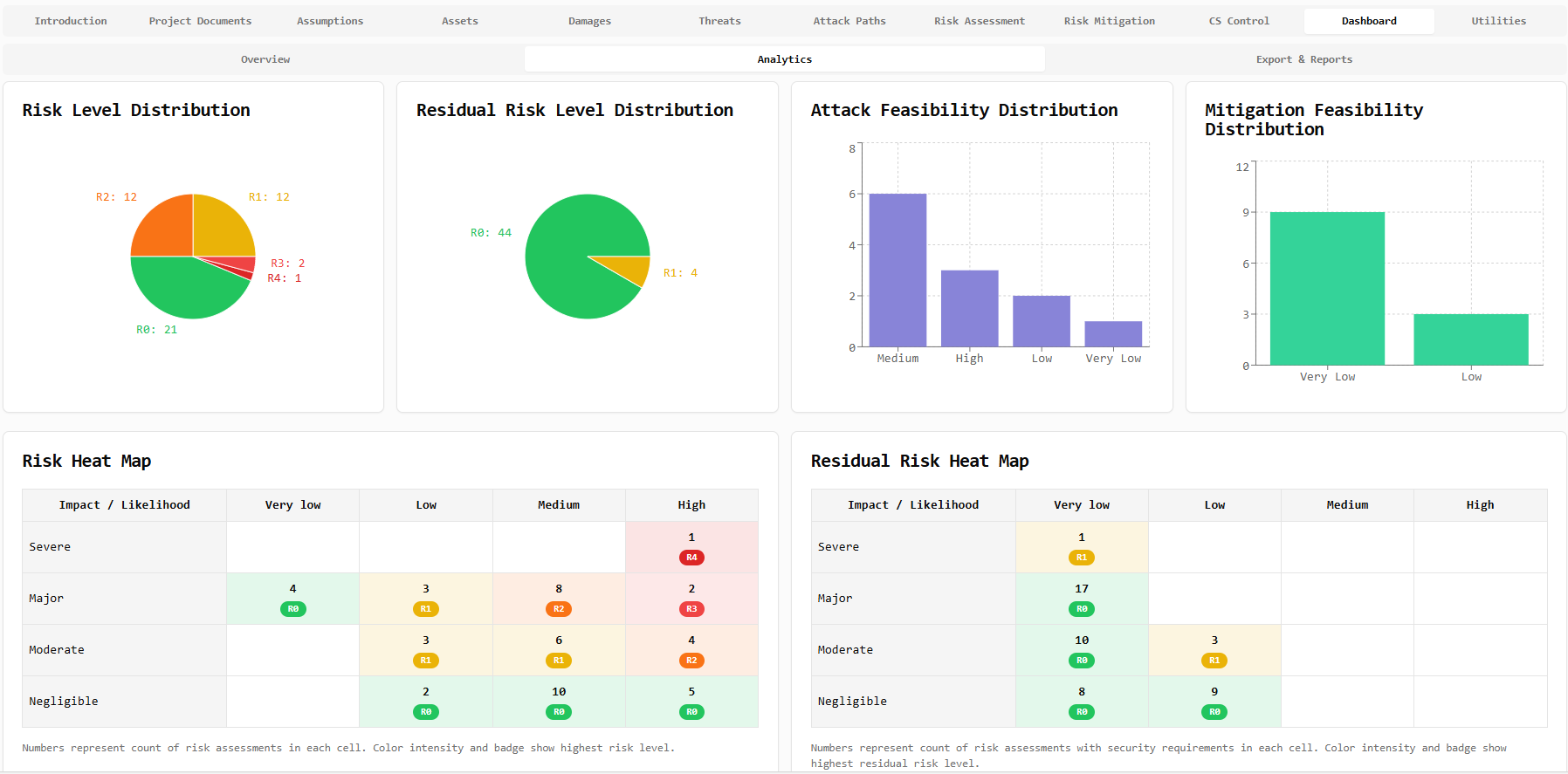
Risk Matrix & Feasibility Scoring
Visualize and prioritize risks with an interactive risk matrix and detailed feasibility scoring across multiple dimensions (Safety, Financial, Operational, Privacy). Our advanced analytics provide clear insights into risk distribution and attack feasibility.
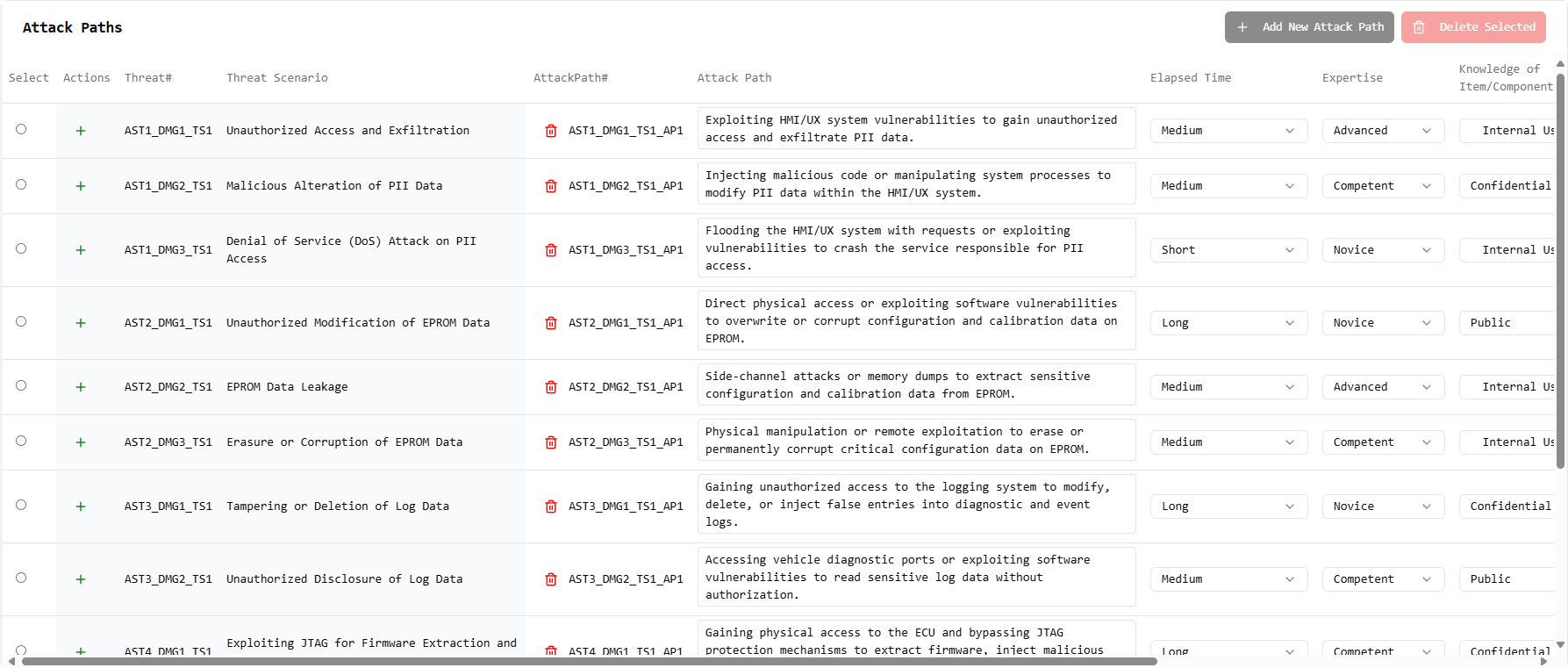
Attack Path Visualization
Map out potential attack paths, understand the steps an attacker might take, and assess their expertise and elapsed time for each path. Visualize the complete attack chain from initial access to final impact.
Attack Paths Analysis
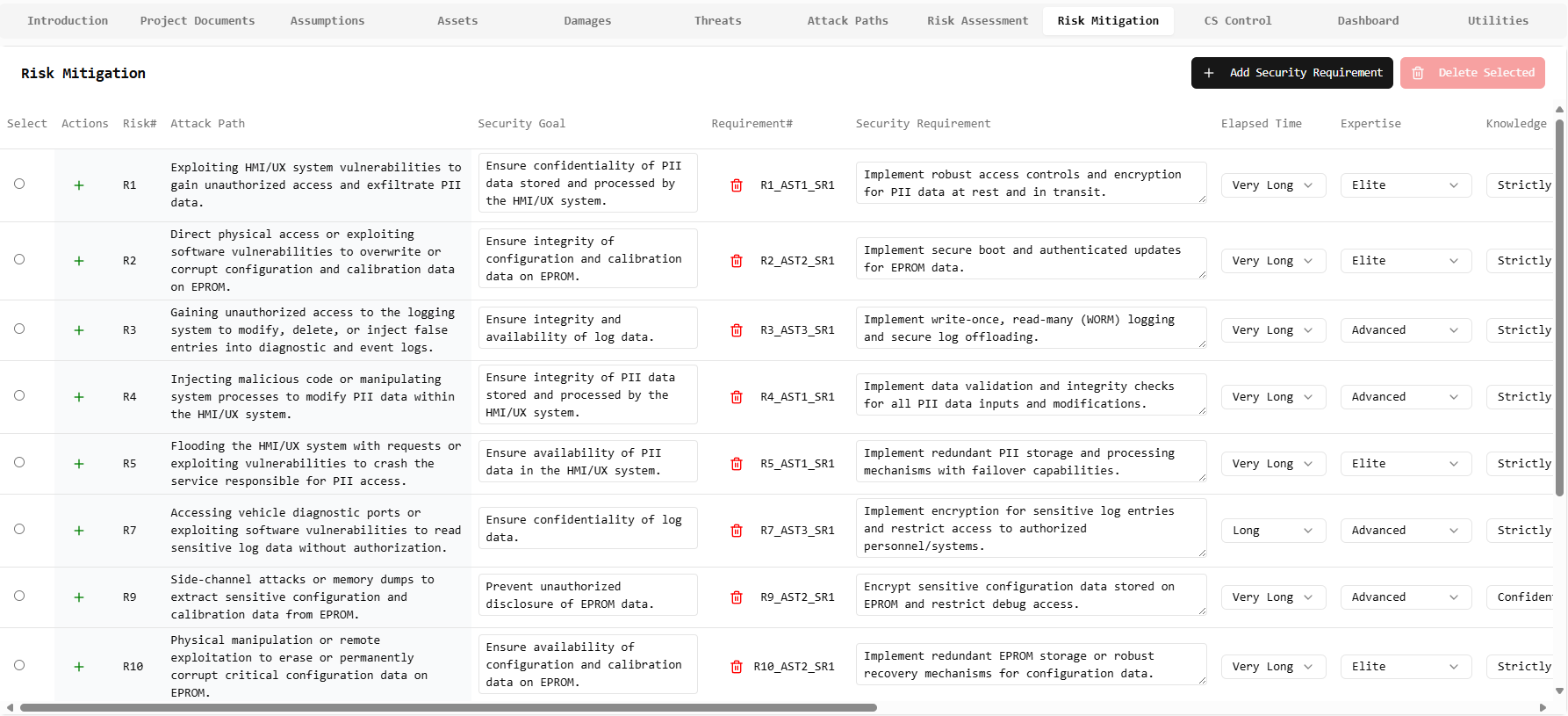
Risk Mitigation
Cybersecurity Controls
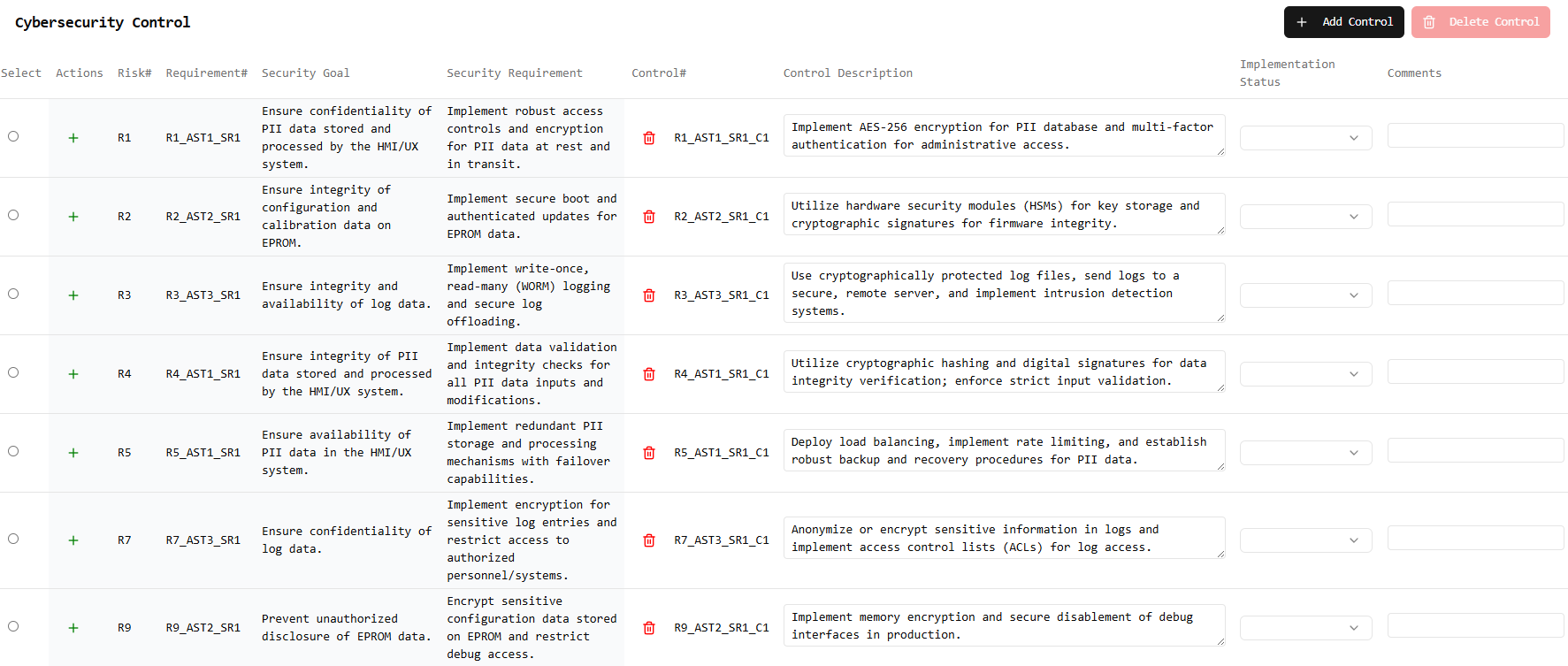
Automated Security Requirements
Automatically generate specific security requirements based on identified risks, ensuring comprehensive coverage and mitigation. Transform risk assessments into actionable security controls and implementation guidelines.
How TaraQuant Works
A continuous, iterative 3-step process for comprehensive security assessment that adapts throughout the entire product lifecycle
Continuous Security: Use TaraQuant to perform incremental assessment - whether you're in development, production, or discovering new vulnerabilities, the process seamlessly cycles back to ensure ongoing protection.
1. Define Assets & Damages
Identify critical assets and potential damage scenarios. Update as new assets are added or threats evolve.
- • Asset identification
- • Damage scenario modeling
- • Impact assessment
2. Model Threats & Attack Paths
Map attack vectors and threat scenarios. Continuously updated as new vulnerabilities are discovered.
- • Threat scenario creation
- • Attack path visualization
- • Feasibility analysis
3. Assess Risk & Generate Requirements
Evaluate risks and create security controls. Triggers reassessment when new risks are identified.
- • Risk matrix evaluation
- • Security requirement generation
- • Mitigation strategies
New vulnerabilities, bugs, or system changes trigger reassessment cycles
1. Define Assets & Damages
Identify critical assets and potential damage scenarios. Update as new assets are added or threats evolve.
2. Model Threats & Attack Paths
Map attack vectors and threat scenarios. Continuously updated as new vulnerabilities are discovered.
3. Assess Risk & Generate Requirements
Evaluate risks and create security controls. Triggers reassessment when new risks are identified.
Process cycles back for ongoing assessment
Initial TARA assessment during design and development. Iterative refinement as features are added and architecture evolves.
Continuous assessment in live environments. New vulnerabilities or operational changes trigger reassessment cycles.
Post-incident analysis and reassessment. Discovered vulnerabilities feed back into the cycle for comprehensive remediation.
Why Continuous TARA Matters
Adaptive Security
Evolves with changing threat landscape
Proactive Defense
Identifies risks before exploitation
Incremental Improvement
Continuous security enhancement
Lifecycle Coverage
From development to production
Trusted by Industry Leaders
Meet ISO 21434 and UNECE R155 compliance requirements with structured threat assessment and risk management for connected vehicles.
Integrate security early in the SDLC with automated threat modeling and security requirement generation for robust applications.
Enhance resilience of critical systems with comprehensive risk assessment and attack path analysis for operational technology.
Empowering Proactive Cybersecurity
TaraQuant was developed to address the growing complexity of cybersecurity in modern systems. Our mission is to provide security professionals, developers, and system architects with an intuitive, powerful, and data-driven platform to perform comprehensive threat assessment and risk analysis.
We believe in shifting security left, enabling early identification and mitigation of vulnerabilities, ultimately building more resilient and trustworthy systems. With TaraQuant, organizations can proactively secure their digital assets and maintain compliance with industry standards.
See how TaraQuant can transform your security assessment process
Get Started with TaraQuant
TaraQuant is open source and free to use. Get started today by exploring our GitHub repository, contributing to the project, or deploying your own instance.
Access the complete source code, documentation, and contribute to the development of TaraQuant.
Get TaraQuant running locally in minutes with our simple installation guide.
Comprehensive guides, API references, and tutorials to help you get the most out of TaraQuant.
Read DocsHelp improve TaraQuant by contributing code, reporting bugs, or suggesting new features.
ContributeJoin our community discussions, ask questions, and share your TaraQuant implementations.
Join CommunityReady to Secure Your Systems?
Start your threat assessment and risk analysis journey with TaraQuant today.